We all know that the privacy and security of our connections are subjects that are increasingly taken into consideration by each of us. Concealment of our real public IP address today is one of the most attractive aspects of the privacy and security of our connections.
People, while browsing the internet, often want to hide their IP address, and the two most common ways to mask the real IP address are:
- Using Tor, a popular anonymity network platform.
- Using proxy servers, or the multi-proxy browser method, where proxy chains with multiple proxies act as intermediaries between your device and the websites you visit.
Both of the above-mentioned methods, i.e., Tor and proxychains (multiple proxies), hide your IP address, but their functions are totally different. Tor uses a complex routing system called “onion routing” based on point-to-point topology and peer-to-peer networks (equipment to masquerade our public IP address), which helps you anonymize your traffic, while multi-proxy browsers create intermediaries between your browser and the website you browse.
Understanding Multiple Proxies With Proxychains
To better understand this concept, here’s a head-to-head comparison.
- Tor
With Tor, it’s like covering the message with several layers of fake IP addresses (onion routing) and passing it through several people (relays) you don’t know. Each person removes a layer, revealing only the address of the next person in the chain. Eventually, the innermost layer reaches your friend, and they know it came from you, but no one else knows the full path.
- Proxy
Usually, people get confused about how to use proxychains. It’s like giving the message to a trusted person (the proxy), who then delivers it to your friend. Your friend knows it came from you, but no one else does.
Without Proxy/Tor: It’s like handing the message to your friend directly. Everyone who sees you deliver it knows who sent it.
While concatenating multiple proxies with proxychains, there are many more elements, including routers, ISPs, and DNS lookups. But at the theoretical level, the issue is that when you connect to the server directly, the server logs will show that the connection has been made using your public IP.
Thus, to avoid providing this information, we use several proxies to perform several IP masquerades. In the below schemes, we will show how to make the IP of your browser by creating a proxychains proxy list:
Here’s the scheme for creating a proxychains proxy list: (The IPs listed in this post are for example):
- Since the IP is 10.1.187.10, we head to the next proxy with IP 200.60.240.10.
- From the proxy IP 200.60.240.10, connect to the next proxy IP 200.60.240.11. This newly connected proxy will see that the source IP connection is 200.60.290.10.
- Again, use the proxy IP 200.60.290.11 and connect to another proxy chain with IP 200.60.290.12; thus, you will see the new proxy IP’s source connection as IP 200.60.240.11.
- Finally, connect to the IP 217.58.210.195; only then will it have been connected to the IP 200.60.240.12.
This process repeats as you connect to additional proxy servers in the chain, leading to multiple proxy servers. Each proxy server only sees the IP of the previous proxy in the chain, not your original IP. Finally, the traffic reaches the destination website (217.58.210.195). The website only sees the IP of the last proxy server (200.60.240.12) in the chain, not your original IP, perfectly masking your IP address.
This also helps prevent the website from tracking your location or identifying you. Knowing the advantages of using multiple proxies, in this blog we will learn to use a tool called Proxychains to easily manage this chaining process.
Proxychains are not installed by default, but installing them on your Linux systems is as simple as typing this command in your terminal:
apt-get install proxychains
With this command, proxy chains and proxy DNS will be installed but they will need configurations. This configuration is done in a file called /etc/proxychains.conf. This file defines two key things:
- How to handle the proxy list, which determines the order in which Proxychains use the proxies you provide.
- The list of proxies itself specifies the IP addresses and ports of the proxy servers you want to use.
How Do Proxychains Use The Proxy List?
There are three ways Proxychains with a multi-proxy browser can handle the order in which it uses your given proxy list. However, it is important to note that only one option can be active at a time among the three. Here are those ways:
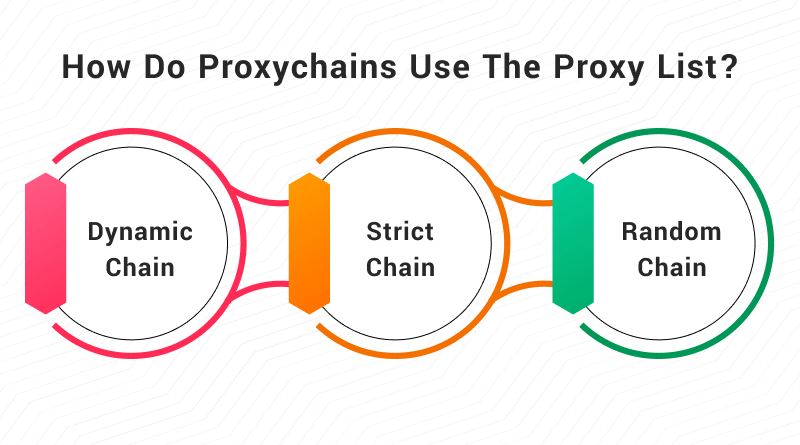
- dynamic_chain: This way of using a proxy list tries the proxies in the order you list them. In case, if any proxy is offline, the proxy chain will jump to the next listed proxy. By default, this option is commented, i.e., it starts with the character #.
- strict_chain: This chain works in a similar pattern to dynamic_chain. But the difference here is that in your proxychains proxy list, there should not be any offline proxy. All the proxies must be online. It is the option enabled by default, although it is usually recommended to use dynamic_chain.
- random_chain: In this case, the connection order does not matter as the proxies are randomly selected to form the multiple proxy server connections.
Enabling Dynamic Chaining In Proxychains
To configure Proxychains to try your proxies one by one, even if some are offline, we need to edit the /etc/proxychains.conf file. Here’s what to do to get the dynamic_chain option enabled and disable strict_chain.
By default, strict_chain will likely be without a # symbol at the beginning, while on the other hand, dynamic_chain starts with a # symbol. So to enable the dynamic chaining, simply remove the # symbol from the beginning of the dynamic_chain line.
Similar is the process for disabling strict chaining. All you have to do is reverse. Just add a # symbol to the beginning of the strict_chain line.
Proxy List Configuration
The configuration file also includes the list of proxies, a section that begins with the nomenclature [ProxyList]. Each line of the list would have a single proxy in this format: Type IP port [password]
In the above format, Type refers to the type of proxy, which can be http or socks5. The IP refers to the address of the proxy server, and the Port is the port number used by it. Lastly, you’ll see the last two fields are placed between [ ], which is the password. It is an optional field required only if multiple proxy requires authentication. That is why these two fields are not mandatory.
Finding Proxy Lists
To know all these details about the proxy list configurations, you can refer to the internet. There are many websites available online from which you can get lists of proxies and their useful configurations.
Adding Proxies to the ProxyList
Once you’ve enabled dynamic chaining, you can add your chosen proxies to the proxychains proxy list configuration file. Here’s an example of adding proxychains that need more proxies (here are two proxy servers) to your configuration:
[ProxyList]
http 134.213.148.8 3124
http 882.082.381.10 3128
Using Proxychains
Once you’ve configured proxy chains and added your proxies, you can use them with various commands and perform network interactions. All you have to do is simply prefix the command you want to run with proxychains. For instance, if you want to open Firefox through the proxy chain, you put the command “proxychains firefox.” Similarly, if you want to download a website using curl through the proxy chain, you need the command “proxychains curl https://www.example.com”
Troubleshooting Proxy Issues
In the case, you have problems with the proxies you added to the proxychains proxy list, try to find alternatives, as not all proxies are created equal. Some might be overloaded, slow, or even offline. Look for other proxy lists online or you can also go with paid proxy services.
Security Considerations with Proxies
Proxy chains hide your IP address, but they don’t guarantee complete anonymity. With this, we would have a much more secure connection that would hide our IP address from the end user. Keep in mind that this technique is designed for benign purposes and that most proxies collect and analyze the connections, so think of this as a protection technique and nothing else.
Using Proxies Responsibly
Finally, it is highly recommended that you choose the proxies you want to use wisely and try to look for them on trusted sites; otherwise, who knows who you could be giving information about your connections?
Online privacy is critical at this time and Proxychains can be a powerful tool for achieving enhanced anonymity and security. Chaining multiple proxies together enables users to effectively hide their actual IP addresses and mask their online identities from being exposed.
In order to continue browsing safely and make the most of it, you have to be cautious while utilizing this technique, following the right principles. Therefore, if you value your privacy and want to browse anonymously on the internet, then try a proxy chain. To avoid compromising your online privacy as well as your security, embrace proxychains that need more proxies and use them responsibly.
I hope this guide has been helpful in understanding proxy chains and their configurations.
FAQs:
What is Proxychains and why to concatenate multiple proxies on it?
Proxychains is a means for diverting your internet traffic through several proxy servers subsequently. It helps you hide your IP address so that it looks like you connect from another location. This might be useful if you want to be more anonymous or bypass geo-restrictions of some websites.
How do I install Proxychains?
Usually, installing Proxychains involves apt-get in Linux systems using package managers. The actual command differs depending on your OS.
Can I concatenate multiple proxies in Proxychains?
It is possible to tell Proxychains to use a chain of proxy servers. Simply change /etc/proxychains.conf file accordingly. This file also allows specification of the order in which the proxies are tried and their kind (HTTP or SOCKS).
Is it possible for ProxyChains to mix HTTP and SOCKS proxies?
Absolutely! Socks5, as well as HTTP, are among different types supported by Proxychains. All that has to be done is write correct type for each proxy in the configuration file.
Does ProxyChains have limit on chaining of Proxies?
ProxyChains does not have any specific limitation regarding the number of chained proxies one can make with it but adding too many would however result in significant network lag. Typically, only a few trusted proxies should be used.