If you’ve been using the Internet for a while now, you must have probably heard of the term “firewall” a lot of times. But many of you might not be aware of what exactly is a hardware firewall and the role it plays.
In this article, we will start with the basics of the hardware firewall, how it works, its benefits and more.
“Firewall” as the name suggests, is a guard that resists fire. A wall designed to stop spreading of fire once it’s started, generally used in huge buildings or between connected structures. Similarly, in the computing environment, a firewall is designed to restrict illegitimate users from accessing the network.
Hardware Firewall- Introduction
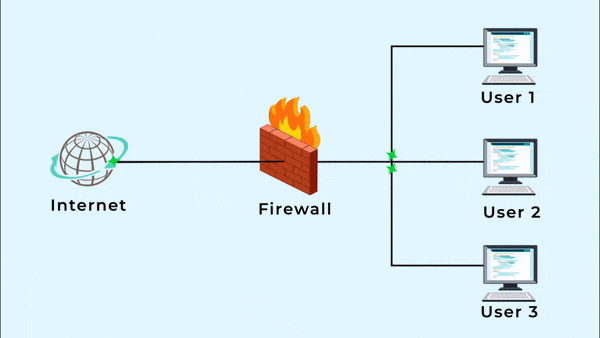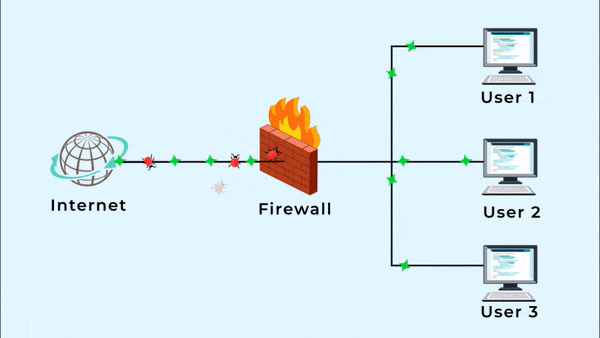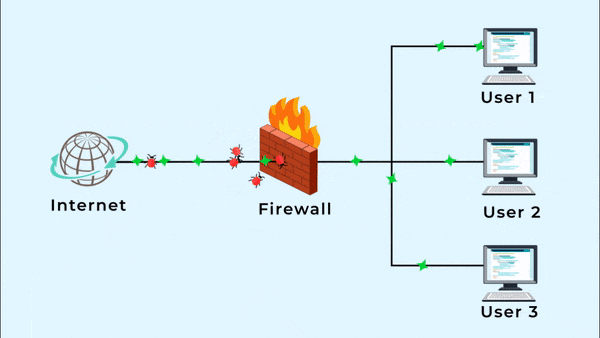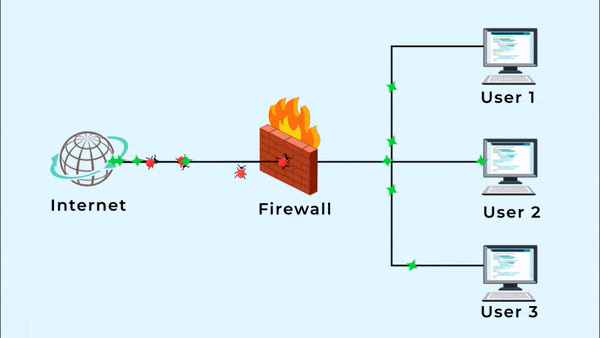
A hardware firewall is a physical device between your computer and the Internet that protects all the computers from any unauthorized Internet users from accessing private networks connected to the Internet. It blocks harmful pieces of data from reaching the system and protects your network against viruses and malware. This means whenever you are accessing the Internet, you have to go through the firewall. A hardware firewall is also known as a network or a gateway firewall.
A firewall’s main objective is to block access to or from a private network. All the incoming and outgoing data packets from the web have to go through the firewall which inspects each packet and obstructs the packet that does not meet the firewall rules. These rules generally include factors like the ports in IP packets, a destination address and a source address.
In short, a firewall screens each packet of data to evaluate where it came from and where it is going and then it takes a decision whether the packet should be accepted or denied.
The router that is generally used for Internet connection is called “network layer firewall”.
However, it does not keep a watch about what a packet is, where it came from and where it goes.
How Does a Firewall Work?
Depending upon your existing network configuration the firewall setup varies. The firewall is directly connected to your uplink and is placed outside your server.
Once the connection to the server is established, the complete traffic coming in or going out from the server will pass through the firewall, making it pass tests. This lets you have full command over the kind of traffic you are receiving and that is extremely important.
There are four mechanisms that the firewall uses to restrict traffic. To provide complete protection one device or application can use more than one of these mechanisms. Let’s take a glimpse of these mechanisms:
Packet Filtering
A packet filter blocks all the inbound and outbound traffic of the network and tests it as per the rules you define. Generally, the packet filter can measure the source and destination IP address, source port and destination port. Based on these criteria you can filter to approve or deny traffic from specific ports or IP addresses. A Packet filter works in the network layer of the OSI model.
Security threats to Packet Filters:
IP address Spoofing:
An external intruder tries to send packets inside the network by using IP address as that of an internal user.
Prevention:
By discarding all the packets coming into the network that has source IP equal to one of the internal IPs, this attack can be blocked.
Source Routing Attacks:
The attacker tries to trick the firewall by sending packets to your network and obtain information about the route it uses by scanning the responses.
Prevention:
By using a path addressing, a firewall can block this attack by discarding all the packets that use source routing.
Tiny Fragment Attacks:
Larger packets are usually broken into smaller ones because of the size limit permitted by the Ethernet. An attacker takes advantage of this feature by creating Internet Protocol (IP) datagram fragments of the original packet.
Prevention:
This type of attack can be prevented by blocking all the packets that use the TCP protocol and are divided. A dynamic packet filter only permits the TCP packets if they are responses to the outgoing TCP packets.
Circuit-Level Gateway
A circuit-level gateway prevents all inbound traffic to itself. Software is then run on the client’s machine to install a connection with the circuit-level gateway machine. For the external network, it looks like all the communication from the inside network is emerging from the circuit level gateway.
Proxy Server
A proxy server is often used to enhance the performance of the network, but it also works as a firewall. It hides your actual IP addresses so that all communications seem to start from the proxy server itself. This type of server caches pages that are requested. For example, if user A goes to Google.com the request is sent from the proxy server and the webpage is retrieved. Now, if User B wants to access Google.com the proxy server transmits the information it already retrieved for User A. Thus, the webpage gets loaded quickly as the information is sent from the proxy server and not Google’s server. With the help of a proxy server, you can block access to specific websites and filter particular port traffic to safeguard your internal network.
Application Gateway
An application gateway is another type of proxy server. A connection is first established with the application gateway, then the application gateway decides if the connection should be permitted or not and then set-up the connection with the target computer. Each communication goes through two connections- client to application gateway and application gateway to the destination.
The application gateway scans all traffic as per the rules before taking a call of passing it ahead. With the other proxy server types, only the address of the application gateway will be seen by the external network, so that the inside network remains safe.
Common Types of Network Attacks
Sniffer Attack
This type of attack has the ability to scan, read, catch any changes in the network and read network packets. A sniffer gets a complete view of the data inside the packets if the packets are non- encrypted.
Denial of Service Attacks(DoS Attacks)
A Denial of Service Attack disrupts normal traffic of the targeted server by flooding the complete server or a computer till the time the complete network shuts down. The attacker can even jam genuine traffic within the network to stop authorized users from accessing the network resources.
DoS attacks the network with the help of common Internet protocols like TCP and ICMP.
Man in the Middle Attack
This attack as the name says, happens when an attacker actively monitors, captures and controls the communication between you and person with whom you are communicating.
Data Modification
Once the attacker gains access to your data, the next action it performs is to modify the data. Without being noticed by the sender or receiver, an attacker can alter the data in the packets. Although if your data may not be very confidential you wouldn’t want any of your data to be changed during the transmission.
 For example, if you are sharing a worksheet with your employees that has names and tasks defined that you do not want the tasks to be modified.
For example, if you are sharing a worksheet with your employees that has names and tasks defined that you do not want the tasks to be modified.
Password-Based Attacks
Password-based access control is typically set for mostly all of the machines in the network. Your access rights define who you are that means your username and password.

The moment an attacker discovers a valid user account, he gets the same access rights as the actual user. For example, if the user has admin-level rights, the attacker also has access to all the controls that an admin has, like creating or deleting accounts or modifying rights, etc.
Once the attacker gains access to your network, he can do any of the following:
- Modify, change routes, or delete your data.
- Acquire a list of all the users and computer names and network information.
- Alter network and server configurations, including access controls and routing tables.
Compromised-Key Attack
To get access to confidential information a secret code i.e. key is required. Even though for an attacker getting a key is quite tough but it is not impossible. Once the key is obtained by the attacker, it is known as a compromised key.

Without the sender or receiver’s information, an attacker uses this compromised key to acquire access to a secured communication. The attacker can even decrypt or alter data using this compromised key. To get further access to other secured communications, they try to use the compromised keys with additional keys.
Application-Layer Attack
This type of attack targets application servers by intentionally forcing the server’s operating system or application to fail. This makes it easy for an attacker to bypass normal access controls. Once the attacker gains control of the operating system or application or network, he can do any of the following:
- Unusually close your data applications or operating systems.
- Add, remove, scan or alter your data or operating system.
- Inject a virus in the network.
- Shut down other security controls to enable future attacks.

To stay safe from such attacks a computer or a network should make use of a firewall within the company so that it safeguards the network and keeps the hackers away.
Firewall Policy and Firewall Rules
A firewall is responsible for making the decision whether the packets should be allowed, denied or discarded based on its rules. A packet is rarely denied, most of the times it is either allowed or discarded. The denied packet is usually skipped because a denied packet uses more bandwidth on its way back and the source assumes that if there is no response from the destination, the packet is dropped and further action needs to be taken (retry or abandon).
If you decide to implement a firewall you must have a good understanding of what it does. For instance, the traffic should be allowed to the web server while denying all the other traffic. This is known as the firewall policy and the person implementing this policy is known as the firewall administrator. The administrator then converts this policy into a combination of technical statements known as ruleset that instructs the software or hardware what needs to be done.
The default setting of the firewall is to deny all the traffic. This is how the Windows firewall works. If you are a Windows user, you must be getting a pop up asking if you want to allow the application to approve the connection of the network. If you click ‘allow’ it will add a ruleset to that particular application that it needs to be allowed. These rules of Windows Firewall can be modified from control panel settings.
Actions that can be taken by the Firewall rules:
- Allow: Allows traffic that matches precisely to the rule and passes it, simply denies the rest of the things.
- Bypass: Permits traffic to go through both- intrusion prevention analysis and firewall. This setting is generally used for media-intensive protocols or traffic starting from trusted sources. This type of rule can be based on traffic direction, IP, protocol and port, etc.
- Deny: Completely blocks the traffic that meets the specified rule.
- Force Allow: Compulsively authorizes traffic that gets blocked by other rules. This traffic allowed by Force Allow rule will have to go through the intrusion prevention module.
- Log only: Only the logs of traffic will be maintained. Action will not be taken.
Types of Firewalls
Proxy Firewall
This type of firewall device is an old type. It serves as the connection between two networks for a particular application. It can provide more functionality like content caching and security by blocking any associations with the outside network. But, it can also affect the flowrate as well the applications it can support.
Stateful Inspection Firewall
Depending upon the protocol, state and port the stateful inspection firewall permits or denies the traffic. It supervises all the activity right from the beginning of a connection until the time it ends.
Unified Threat Management (UTM) Firewall
A UTM firewall provides advanced protection and allows users to take full control and manage network security with less complexity. It protects the network from malware, malicious attachments or viruses by scanning the incoming data using Deep Packet Inspection.
Next-Generation Firewall (NGFW)
From simple packet filtering to stateful inspection, firewalls have made a lot of progress. Many businesses are moving towards next-generation firewalls to remain safe from modern-day threats such as application-layer attacks and advanced malware.
A next-generation firewall must contain:
- Comprehensive intrusion prevention.
- Enhanced paths to take into account for future information feeds.
- Standard firewall ability like a stateful inspection.
- Methods to overcome growing security threats.
Although the above-listed capabilities have become the standard for most of the organizations, NGFWs has the ability to do a lot more.
Threat-Focused NGFW
A threat-focused firewall includes all the features as that of a traditional next-generation firewall along with some advanced threat detection and solution.
A threat-focused NGFW provides the ability to:
- Figure out which assets are at higher risks with full context-awareness.
- Perform actions to respond to attacks with modern security automation.
- Determine suspicious activity.
- Improve the time duration from detection to cleaning up with advanced security that endlessly monitors for suspicious activities.
Benefits of Hardware Firewall
1. Port Access
You get complete control to modify rules with options such as allowing all traffic to your website or keeping SSH access only to the developer and yourself.
2. Traffic Control
You get the ability to decide what kind of traffic shall reach your server and which type of traffic to block.
3. Managed Equals Control
Have access to adjust controls, configure and troubleshoot for the complete staffed networking team.
4. Default Rules
List of fully configurable default rules that can be applied to all traffic.
5. Additional Server Resources
Get complete control of additional server resources that can be made use of. Even the software firewall can be disabled from your server and you can fully depend upon the hardware firewall for complete protection.
Related- Difference Between Hardware Firewall And Software Firewalls
Wait…Before You Choose Your Firewall
Purchasing a firewall is similar to buying a car. Not one car fits all family sizes and needs. There are different factors that you need to consider before buying a car. A family of 6 won’t be comfortable in a basic 5 seater car and it will not make any sense to buy a minibus. In the same way, buying a firewall requires detailed research before deciding on your purchase.
Here are some basic questions that you should go through before buying a firewall:
1. What is the Size of Your Business?
Depending upon the number of users in your network, the size of the firewall will vary. This means, the more the number of users in your network, the larger the firewall. Most firewalls cannot be upgraded so it’s better to consider a quite larger one than you need.
2. What Type of Business Do You Run?
If you run a business that requires single-handed based working and doesn’t contain any sensitive information then a software firewall will be adequate. But say, if your company is a financial firm then a powerful firewall will be required.
3. What Type of Firewall Do You Need?
Each firewall has its pros and cons. Do a proper research and take help from experts before making your decision. The types of firewalls are already explained above.
4. Will You Need Any Anti-Virus Software?
Yes. Even after installing a firewall you will need anti-virus for your system. Because, malicious threats like viruses, trojan horses, worms can only be detected with the help of a firewall. These viruses can enter from external sources like SD cards, DVD’s, emails, USB, etc.
5. Do You Need Virtual Private Networking (VPN)?
A VPN lets you log in to a secure network remotely. It can be IPsec for a site to site Internet Protocol Security that lets you connect to remote company locations or third parties. An SSL VPN may be required to allow a secure connection to your resources for your local and roaming workers. The number of workers in your remote network will impact the type of firewall you may need and its price.
6. Do You Need Identity Management (IDM)?
IDM is the process of identifying, authenticating and authorizing the identity of an individual user or a group of users on a network. A standard firewall usually can only implement policies and record traffic against IP addresses while the advanced firewalls such as UTMs and NGFWs can integrate with directory services so that the rules or policies can be applied and traffic recorded for users and user groups.
Things to Take Into Account
Security

A lot of people are selling UTM devices. Some of these devices include a wide range of features at high prices whereas some of them include only important features at a lesser cost.
Make sure that you select a well-known and trusted platform. Cisco, WatchGuard, Barracuda, and SonicWALL are reputed names in the market and the reason that they’ve earned this value is that they are reliable and secure. No matter which one you choose to ensure that the firewall is ICSA certified. ICSA (International Computer Security Association) is the industry standard for packet inspection.
Remote Users
 With the ongoing trend of work from home in almost all businesses, employees should be able to access your internal network from any location. It can be from home, a cafe, a library, parking, or a coworking space they should be able to establish links to the network and finish their tasks.
With the ongoing trend of work from home in almost all businesses, employees should be able to access your internal network from any location. It can be from home, a cafe, a library, parking, or a coworking space they should be able to establish links to the network and finish their tasks.
Cost

When buying a firewall cost is always a factor that one must consider. It’s not only important to know how much is the cost but it is also important to figure out how it will fit into your budget.
Generally, we tend to ignore the consequences that might occur if we don’t purchase something that was needed. By the time things go wrong, you are already into a big loss than just the money.
The old or traditional firewall may deliver an average performance or reduced efficiency but modern firewalls are worth spending when it comes to a network security breach.
Real-Time Alerts

Catching an ongoing attack is important on today’s date. But if you think that it has nothing to do with a firewall, you may be wrong. A lot of firewalls these days provide a range of options that give real-time updates about any harmful activity. This helps the company to quickly take action on any vulnerable patches within their network.
Interoperability

The IT security solutions these days require a multi-layer approach that has a range of technologies like intrusion detection and prevention system, anti-malware or antivirus software and more.
A next-generation firewall will engage with most of these technologies like access control products, network monitoring tools, external web and email security solutions and authentication servers.
Different firewalls may have different levels of compatibility with these tools, helping businesses to check that they pick a solution that can effortlessly sync with their other security products.
Content Filtering

A standard firewall offers you limited access and control of the applications and outside users accessing your network.
You may not want all the users to have access to social media sites like Facebook, Twitter, etc. but what about your marketing department? A traditional firewall may not let you apply policies separately to different users whereas with advanced firewalls you can apply policies to specific users or even group of users.
Next-Gen firewalls can do a lot more when it comes to permitting or denying access to applications. For example, a user may be able to use Pinterest to search and add pins to boards but he may not be able to post any new pins on the platform.
User Name Not IP Addresses
Modern firewalls have the capability to find any device with its user name instead of finding using the IP address.
This helps you to discover an exact number of devices each of your users is using to access the network and if they violate the rules you can easily locate the device and take necessary action.
Technical Support

Hardware failure is not very rare. Even a newly brought device may malfunction or cause troubles. While you purchase to make sure they provide 24/7 technical assistance so that you get help for your device when it fails.
Here’s a quick tip: Ask questions about configuration and deployment of the firewall. The accuracy of their answers to your queries will help you decide whether the brand is reliable.
Wireless Security

Although you may not think it’s needed, you must consider hardware-based firewalls that possess wireless network features. While deploying you can install it with the wireless service disabled. At the point of time when you need to add it, your cost for new purchases (which are higher) will be saved for wireless security and enabling it is just a matter of few clicks. As your company grows, your need for wireless security may arise at any point in time and WLAN security will become essential.
Failover
Most of the businesses need WAN failover or Internet connections that has automatic error detection and fixation. Some firewalls may not provide automatic failover support. If you are in an organization that requires such feature then ensure the model you select incorporates failover. Also, don’t expect that the high-end firewalls have this feature by default. Each one has a unique feature to meet the needs of different types of networks.
Top 10 Hardware Firewalls
1. SonicWall TZ400 Security Firewall
This is an entry-level business model firewall, perfect fit for a small to midsized company.
SonicWall is widely popular for manufacturing top-notch firewall products and undoubtedly TZ series are unbeatable.
SonicWall TZ400 provides a cloud-based and network monitoring system to provide you with a complete security solution, along with software antivirus. The UTM – Unified Threat Management system gives them the ability to offer enterprise-grade network security.
To get complete benefits of all UTM software security features, you will need a license subscription the same as you need for other UTM firewalls.
It can support more than 100 additional products when incorporated with the Dell X-series network switches.
The key feature of this firewall is that it can perform deep packet inspection of complete Internet traffic without affecting transfer speeds. All this is possible because of the processing power of this device. The actual speed of WAN connections is 900 Mbps with 1.3 Gbps throughput.
2. Cisco Meraki MX64W
Cisco is the top-most manufacturing company in enterprise-level networking solutions. To serve the wireless LAN products for SMBs, Meraki was bought by Cisco.
Meraki MX64W offers a hardware firewall and WiFi router with excellent Internet security features.
With layer 7 application visibility, it scans and filters traffic without reducing bandwidth.
It supports 250 Mbps firewall throughput and 1.2 Gbps Wifi speeds. The users in the network can access fast Internet connections.
Just by paying some additional amount Cisco also offers advanced security services such as Cisco Threat Grid, advanced content filtering and advanced malware protection.
3. FortiGate 30E
Unlike a typical firewall, FortiGate 30E offers a lot more. With features like NGFW (NextGeneration Firewall), DNS Filtering, IPS (Intrusion Prevention Scanning), Threat Protection, SSL VPN, Web Filtering, AntiVirus Scanning along with WAF (Web Application Firewall).
Related- What Is A Web Application Firewall?
Fortinet schedules even let you configure firewall policies that can be applied for specific hours. For instance, you can even block access to social media for your users except between their break hours.
FortiGate 30E is a durable device with a top-level of performance and security. This firewall is ideal for all small businesses that require high security and visibility more than what is offered in the ADSL / VDSL modem/router present in the firewall.
4. WatchGuard Firebox T15
Firebox T15 is best suited for small-scale industries as it offers strong security measures at reasonable prices.
WatchGuard’s Firebox T15 firewall device provides application controls, IPS, web content filtering, gateway antivirus (AV), anti-spam, reputation enabled defense and network discovery. With their Gold support subscription, it also enables DLP (Data Loss Prevention), APT (Advanced Persistent Threat Blocker) and Dimension Command.
5. Sophos UTM
In addition to UTM functionality, it offers some advanced features such as App control, URL Filtering, Email, Intrusion Prevention, Anti-virus and built-in Wireless Controller.
They also offer protection for the unlimited IP addresses and incorporated with features like Stateful Packet Inspection, DNS and proxy server, VPN and Network Address Translation.
6. Protectli Firewall Appliance
The Protectli Firewall Appliance is integrated with the Intel Quad-Core Celeron processor with a 32GB SSD drive and 4GB RAM. This ensures that any open source firewall runs smoothly on it.
Protectli Firewall contains 4 gigabit Ethernet ports, with LAN and WAN port that connects your device to a home network.
To install and configure this device, you will need to have in-depth technical knowledge as it utilizes open-source software firewall distributions. This device is designed especially for expert users having hands-on such devices.
OpenVPN, pfsense, dd-wrt, ClearOS, FreeBSD, CentOS are a few open-source firewalls and software that can be installed on this module.
7. Palo Alto Hardware Firewall:
Palo is a leading name in the NGFW firewall and is perfect for large enterprises. The key features of this firewall are high speed and high performance. It has some very good features such as Exploit Protection, Automated Correlation Engine and SaaS Enforcement.
For huge organizations, Palo Alto and Checkpoint are more reliable and fully-featured among all the other firewalls. Depending upon your business needs, you can choose any one from them. Key features of the Palo Alto Firewall:
-
-
- Data Filtering and Policy Control.
- User Visibility and Control.
- Application Visibility and Control.
- Advance Persistent Threats Prevention
- Exploit Protection.
- Intrusion Prevention System.
- Automated Correlation Engine.
-
Checkpoint Hardware Firewall:
Checkpoint – The first stateful firewall of the world is yet another big name for large enterprises. Right from 1969 checkpoint, firewall acts as the primary security shield for big networks. It provides a three-tier architecture with some advanced features.
Key features of the Checkpoint Firewall:
-
-
- URL Filtering
- Identity Awareness
- Mobile Access
- Content Awareness
- Firewall and IPSec VPN
- Advanced Networking & Clustering
- Antivirus, Anti-Spam, Anti-Bot
- IPS and Application Control
- Data Loss Prevention
- SandBlast Threat Emulation and SandBlast Threat Extraction
-
Checkpoint contains a big client database of large enterprises. Although this firewall is quite pricey but it offers great security as compared to the price we pay. In the end, there is nothing more important than security of your network.
Cisco ASA firewall
The ASA in Cisco ASA stands for Adaptive Security Appliance reason being that the ASA device provides flexible security features and to meet specific requirements it can be adapted for small as well as large networks.
Cisco ASA is a whole package that combines intrusion prevention, antivirus, firewall and VPN. It has a built-in threat defense system that blocks attacks before they spread through the network.
Features:
-
-
- Multilayered protection
- State-full Failover
- Simplified management and lower costs
- Unified security services and task automation
- VPN Load Balancing
- Wide range of sizes and form factors
- User Base Authentication
- Modular Policy Framework
- Multi-Context Firewall
- Dynamic Routing protocol support
- ASA Clustering
- Firepower services
-
10. Juniper Networks SRX
The SRX series firewalls offer high-performance security, flexible connectivity, routing and network solutions for organizations.
To deliver high security, the SRX Series particularly offers application visibility and control, next-generation firewall, IPS and some additional security services.
Key Features:
-
-
- Scalable performance
- Network segmentation
- Robust routing engine
- Interface flexibility
- System and network resiliency
- Comprehensive threat protection
-
Conclusion
There often comes a question of whether you should use a hardware firewall or software firewall. The answer is simple, you can run both of these firewalls parallelly. After all, hardware or software firewall does the same task. Both of them act as an obstruction between the Internet and the computer and blocks any harmful attacks from reaching the system.
We have covered all the basics of a hardware firewall and hope that it has given you a clue of how they operate, their types, its advantages and more.
If you’re looking to enhance the security of your network, pick the one from the list or get in touch with our team and we can offer you the best firewall that perfectly meets your security demand.